To successfully install the Gladstone360 Access Control Windows Service, the following prerequisites should be considered.
Whitelist the Gladstone360 API URL and File Paths
Ensure that the API URL and all relevant folder and file paths are whitelisted. Take into account access to the API URL from the PC as well as any firewalls or proxy servers that may be in place. This step is crucial to allow seamless communication and data exchange between the access control system and Gladstone360 API.
Enable Communication over Port 443
Allow communication over port 443 on the PC. This port is used for secure web communications (HTTPS) and is required for accessing and managing the access control system. Enabling communication on this port ensures a secure and reliable connection between the PC and the Gladstone360 API.
Provide File Upload Capability
Grant the ability to upload or copy the Gladstone360 Access service installation file, FTDI driver (used to convert the USB port on the PC to a virtual communication port) and the communications test port application to the PC. This will facilitate the installation process and allow for testing the communication between the access control system and the PC. It is important to ensure that the necessary files and tools are readily available for successful deployment and configuration.
Where Applicable - Enable Remote Access for Engineers
Arrange for remote access to the PC attached to the Access Control Communications Box for the Gladstone Engineers. This can be achieved through third-party applications such as WebEx or TeamViewer. However, Microsoft Teams cannot be used as it may lack the required functionalities. Remote access enables engineers to perform necessary tasks, troubleshoot issues, and provide support without physical presence.
Grant Onsite and Remote Access for Engineers
Provide engineers with a login account that has the necessary rights and permissions to install the Windows Service, start and stop the Windows Service, create folders, and update the service configuration file. This access is crucial for proper installation and configuration of the Gladstone360 Access Control Windows Service.
Windows Service Account
Note that the default user running behind the Windows service is the Network Service account. However, if this account does not have internet access and the necessary permissions to communicate with the com port, a new user account will need to be created. The new account should have the rights and permissions to access the Gladstone360 API URL and communicate with the com port. It is essential to verify and configure the user account settings to enable the access control system to function correctly.
Preconfigure Active Membership Cards/Fobs
Ensure that a minimum of two preconfigured active membership cards or fobs are available. These cards or fobs will be used to test the access control system. By having preconfigured cards or fobs ready, the system can be properly evaluated for functionality and performance.
Educate Staff on Access Control Override Disabling
Ensure that staff members are knowledgeable about how to disable the Access Control override. This knowledge is important during the testing phase as this will need to be disabled to confirm functionality.
Arrange for Testing and Access Control Validation
Designate a staff member who will be available to test access control by tapping the card on the reader. This testing should be scheduled at a suitable time. During the testing period, the turnstile or gate override should be switched off to lock the gates, ensuring that users cannot enter the area. This validation process will help confirm the system's functionality and identify any potential issues or improvements.
By addressing these prerequisites, the installation and operation of the access control system can be effectively implemented while ensuring security, functionality, and user satisfaction.
Gladstone360 Access Control Sequence Diagram
In the sequence diagram below, each step is represented by a lifeline (vertical line) and the interactions between the lifelines are depicted using arrows.
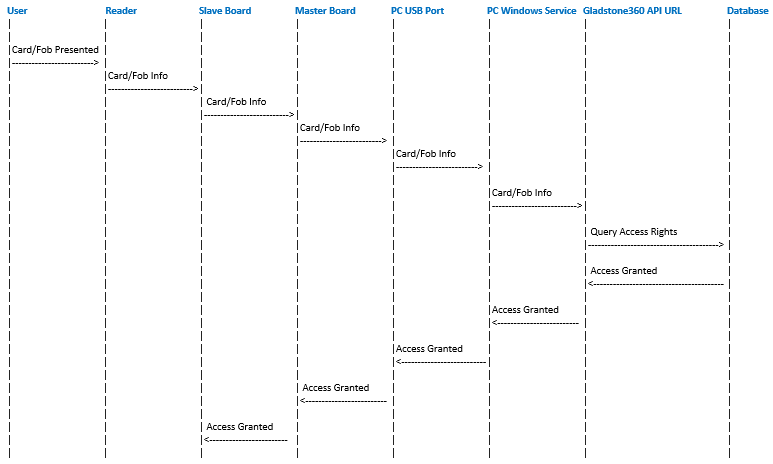
User: Staff or members of public
Reader:Hardware which is connected to the turnstile used to read the card/fob
Slave board:Physically connected to the turnstile
Master board:Located within the communications box (this box will be near the PC). The master board is connected to the slave boards on the turnstiles and the USB port on the PC
USB Port: Located on the PC and facilitates communication between the master board and the Gladstone360 Access Control Windows Service
Windows Service: The Gladstone 360 Access Control Windows Service facilitates the communication between the Gladstone API and the master board
Brief explanation of the steps:
- The User presents a card or fob to the Reader on the turnstile.
- The Reader retrieves the information from the card or fob.
- The Reader passes the card/fob information to the Slave Board.
- The Slave Board forwards the card/fob information to the Master Board on the communications box.
- The Master Board sends the card/fob information to the USB Port/Virtual Com Port on the connected PC.
- The USB Port/Virtual Com Port transfers the information to the Windows Service running on the PC.
- The Windows Service passes the card/fob information to the Gladstone 360 API.
- The Gladstone360 Access API is responsible for checking the user's access rights within the Database.
- The Database performs a query to determine if access should be granted or refused based on the user's rights.
- If access is granted, the result is sent from the API to the Windows Service.
- The Windows Service communicates the access allowed decision back to the USB Port.
- The USB Port transfers the access allowed decision to the Master Board.
- The Master Board relays the access allowed decision to the Slave Board.
- The Slave Board triggers the entry point to open if access is granted.
If access is denied, no information is exchanged between the service and the USB Port/Virtual Com Port and the users access is denied.
